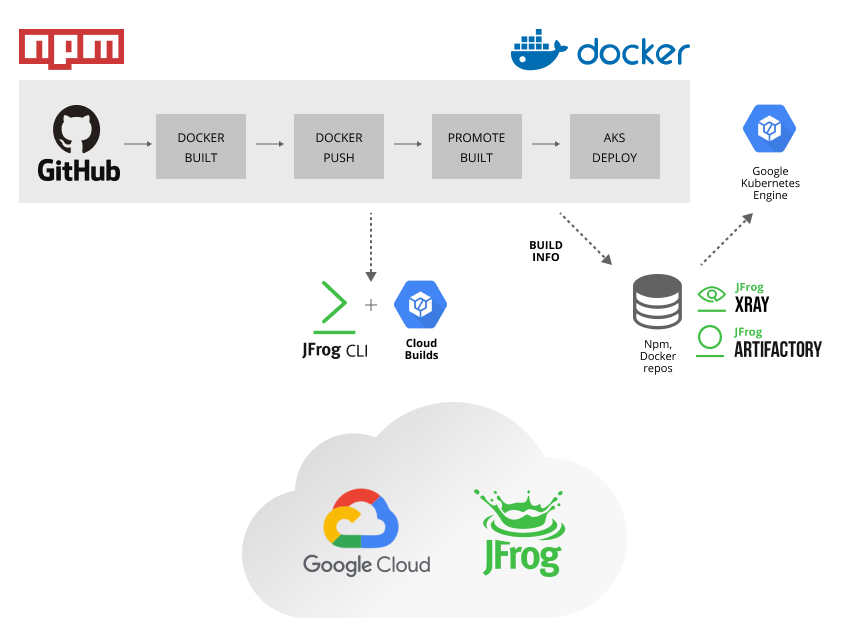
Build and Deploy the NPM Application Docker Image
Now, we can use new JFrog CLI image to build the NPM application Docker image and push it to Artifactory’s Docker repository using Cloud Build Trigger.
-
Return to your Google Cloud Shell terminal and change directory to gcp-gke-workshop/workshop-app.
-
Use Google Cloud Build, trigger and the JFrog CLI to build the NPM Docker image. The cloud build trigger uses cloudbuild.yaml. If you look inside this file, you will find it performs following steps:
jfrog config addconfigure the JFrog CLI to access our JFrog Platform instance.jfrog npm-installuse JFrog CLI to perform npm install to collect and validate NPM dependencies.jfrog npm-publishpublish the npm all to npm repo in artifactory.jfrog build-publishuse publish the build info.docker buildbuild docker image of the NPM application.docker pushpush the newly created image to Artifactory’s Docker repository.create releasecreate release in Cloud Deploy which deploys the app from artifactory in GKE.
The JFrog CLI is used to collect build information during this process and publish it to Artifactory.
- Before triggering the Cloud Build, remember the kubernetes cluster we created in the beginning of the lab? It must be ready by now. Let’s establish connectivity to it with the following command
gcloud container clusters get-credentials gcpworkshop --project=$PROJECT_ID --zone=$ZONE
- Verify that our cluster is healthy and by showing the Kubernetes nodes.
kubectl get nodes
- We need to set our Artifactory registry credentials in order to pull the NPM application image. We will do this my creating Kubernetes secrets. Execute the following command, substitute your server name and JFrog Platform credentials (username and API key).
kubectl create secret docker-registry regcred --docker-server=$JFROG_SERVER_NAME --docker-username=$JFROG_USER --docker-password=$JFROG_API_KEY
-
You have to create this secret in other 2 clusters also: testgcpworkshop and staginggcpworkshop.
-
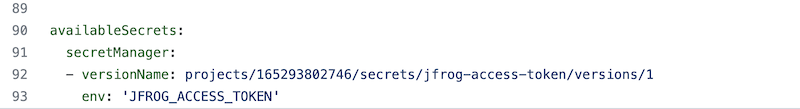
Now edit the cloudbuild.yaml in your fork to update versionName for access token secret which we have saved from 4.24 step and commit to trigger cloud build.
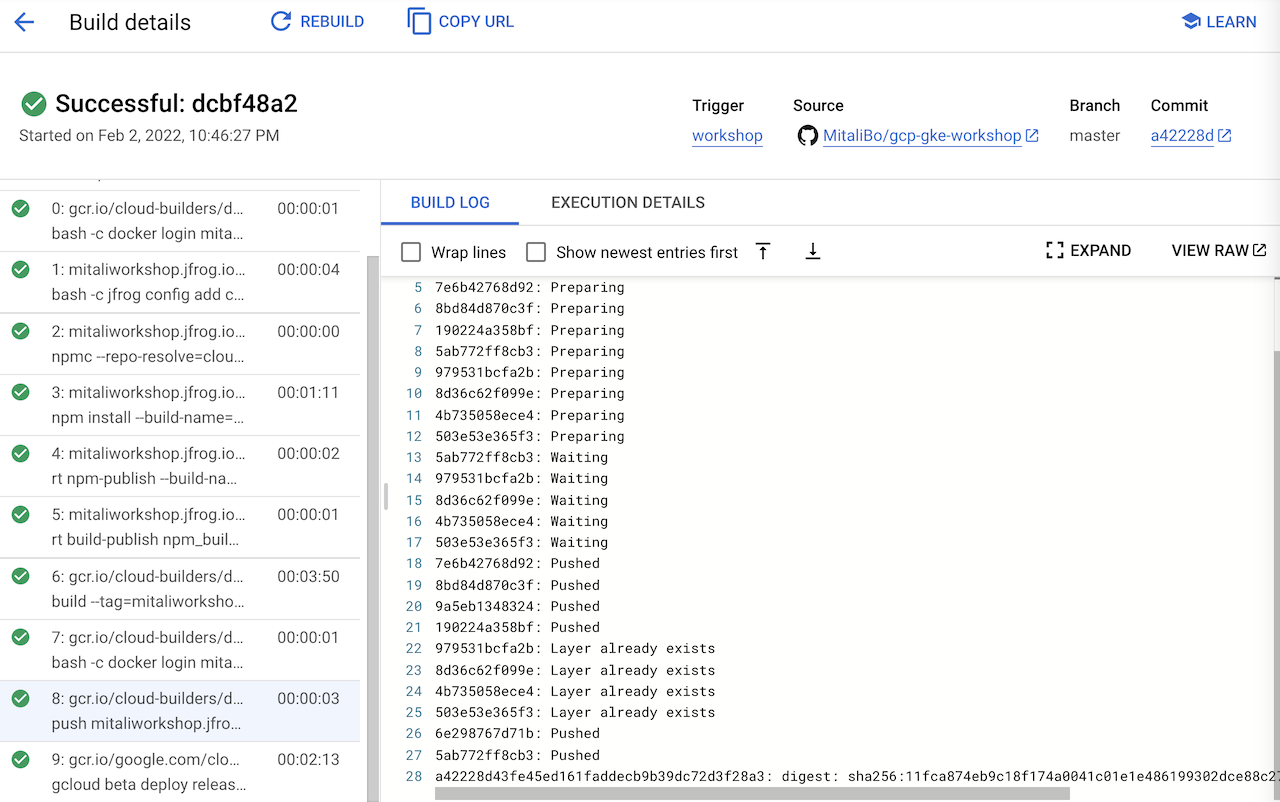
If above cloud build passes all steps then it should result in a successful build of docker image which should be pushed to Artifactory.
Also the cloud build should create a release in Cloud Deploy pipeline and Deploy the app to test.
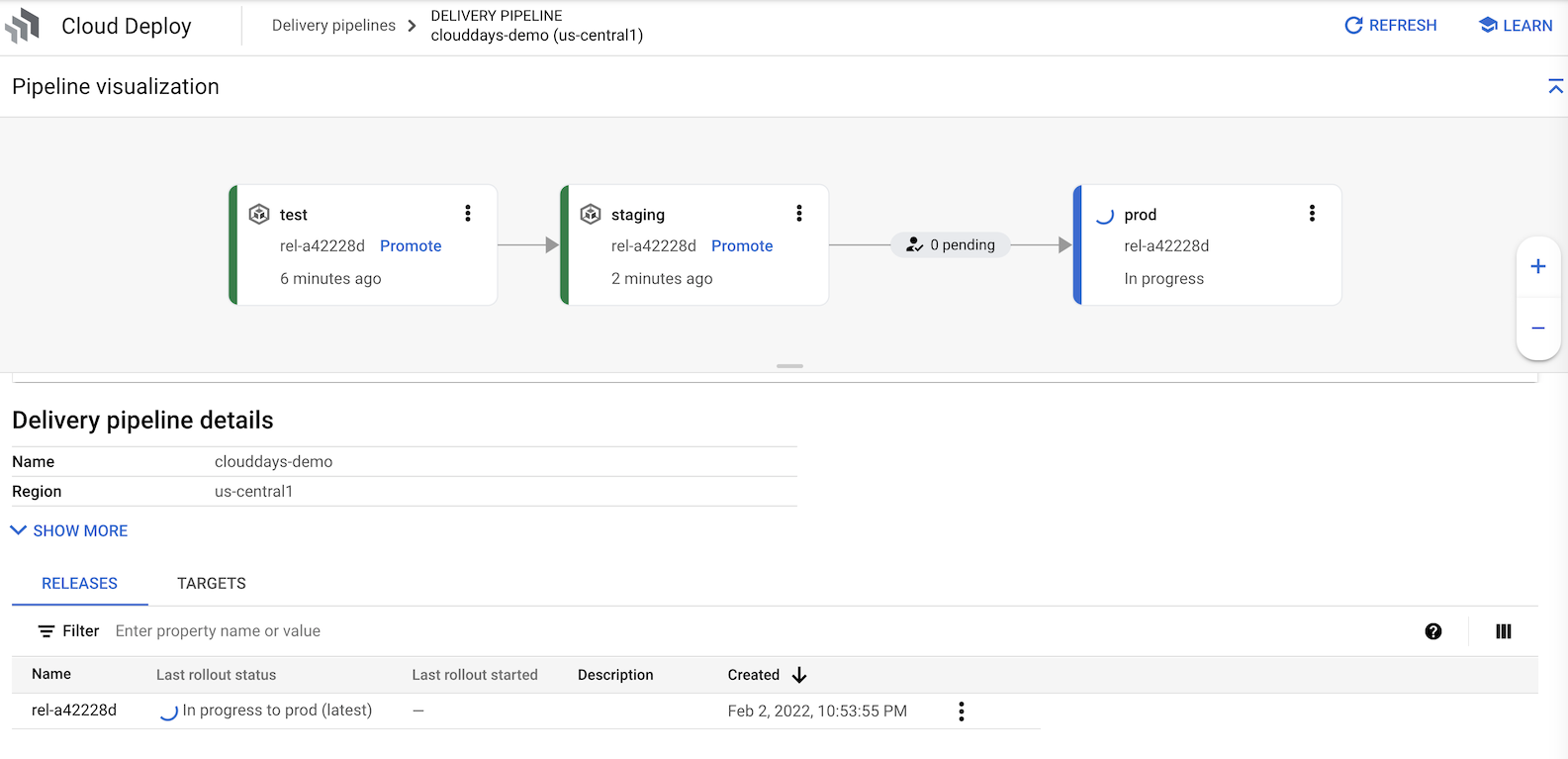
- Execute the following to see your deployed pod.
gcloud container clusters get-credentials testgcpworkshop --project=$PROJECT_ID --zone=$ZONE
kubectl get pods
You should see you npm-app pod.
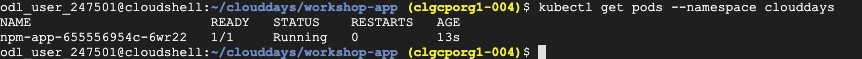
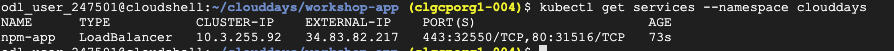
- Now let’s get the external IP so that we can view your application. Execute the following.
kubectl get services
This will provide the EXTERNAL-IP.
-
In your browser, go to https://<EXTERNAL-IP> to view your deployed web application.
-
Click through the self-signed certificate warning. You should see the following web application.

 .
. .
.