View Results in JFrog
We have built and published our NPM package and Docker image. Let’s view these results in JFrog Artifactory.
-
Go to your JFrog Platform instance and switch to the Packages view in Artifactory. Go to Artifactory ► Packages.
-
Type
workshop-appand search. This will show the NPM package that was published with the JFrog CLI. -
Click on it to view the details.
-
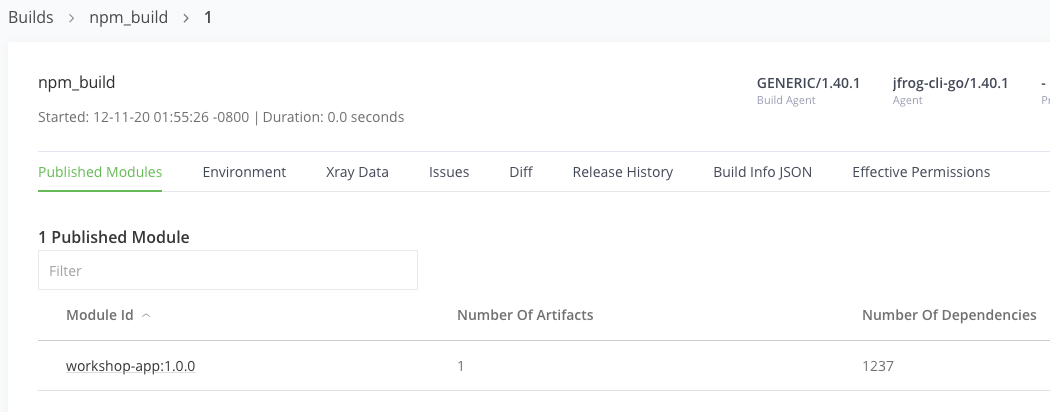
Click on the workshop-app:1.0.0 under the Published Modules tab to see the artifacts and dependencies.
-
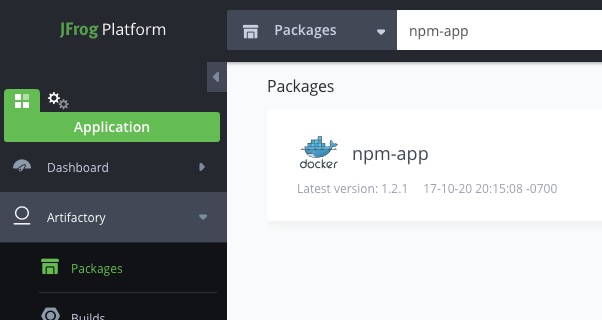
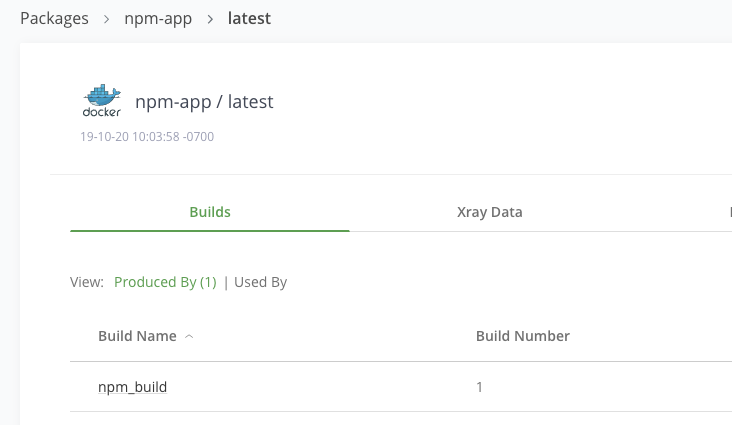
Go back to the Packages view and search for
npm-app. This shows the Docker image that was published. -
Click on the docker npm-app listing.
-
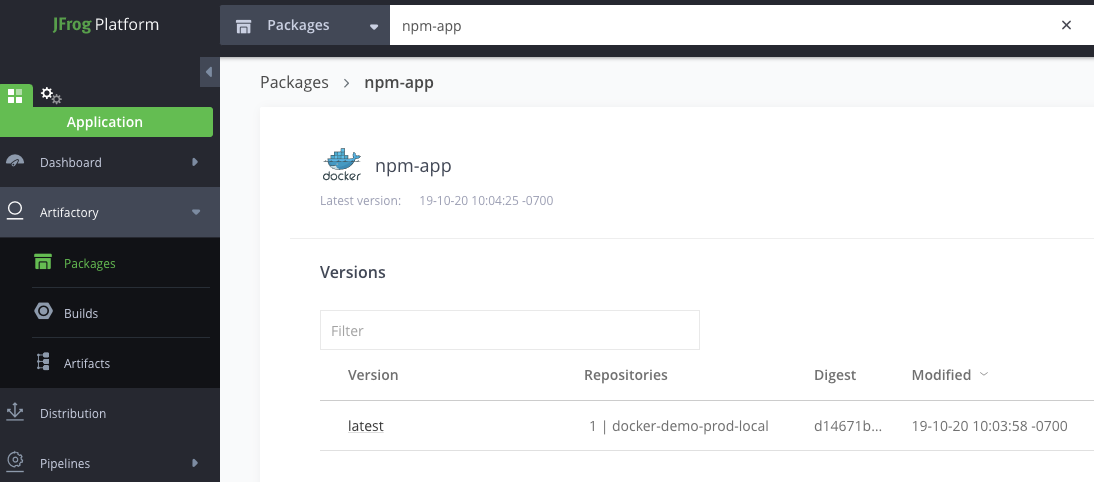
This will show a list of the versions. Click on the latest version that was built.
-
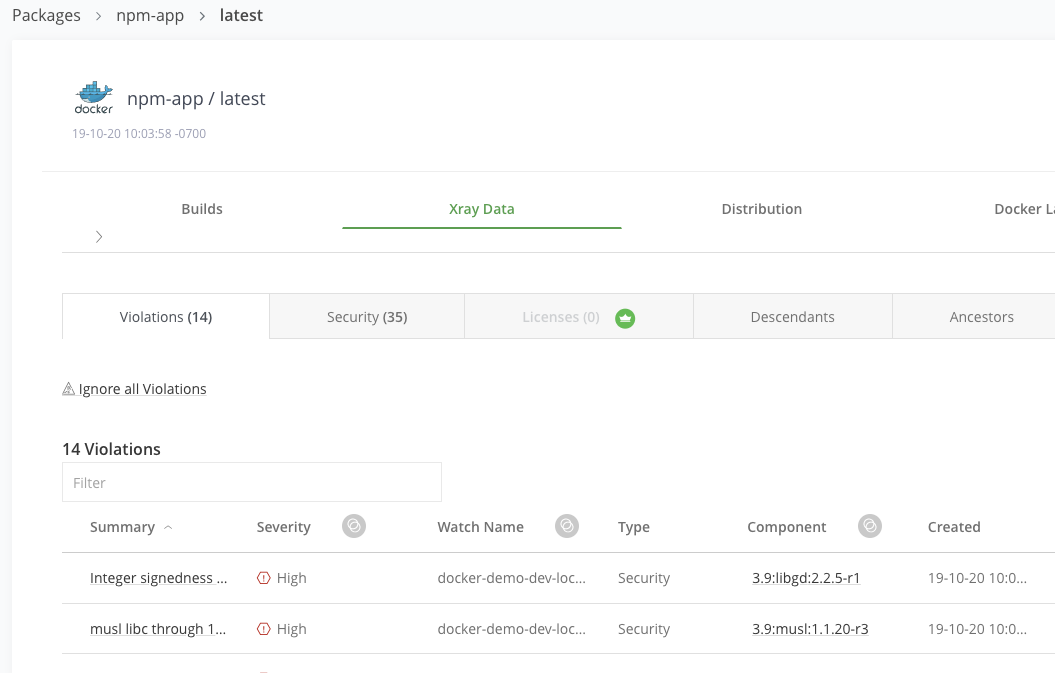
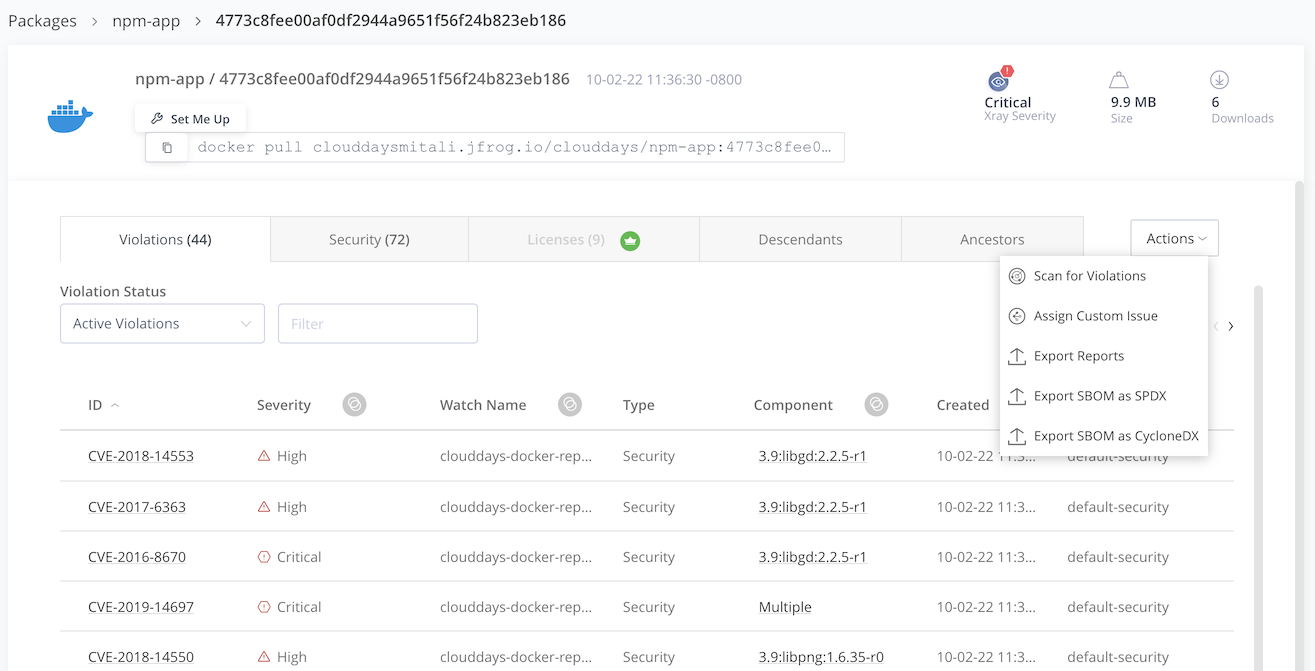
In the Xray Data tab, view the security violations. License violations are available in the JFrog Platform Pro and Enterprise tiers.
-
Click on Actions drop down and you can download SBOM as SPDX or CycloneDX.
-
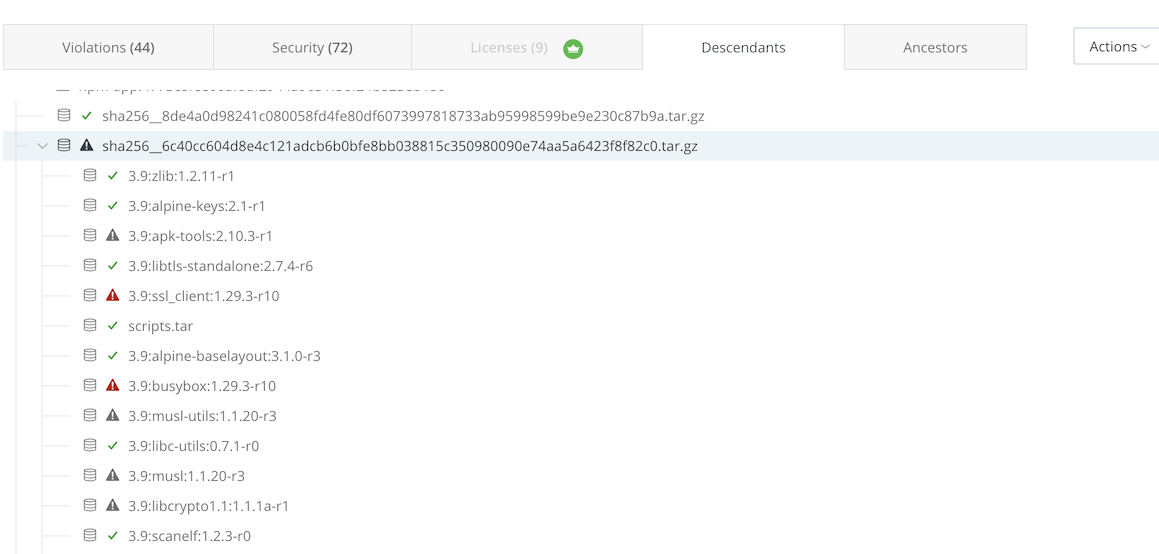
Click on Descendants tab to see at which particular layer your softaware is infected.
-
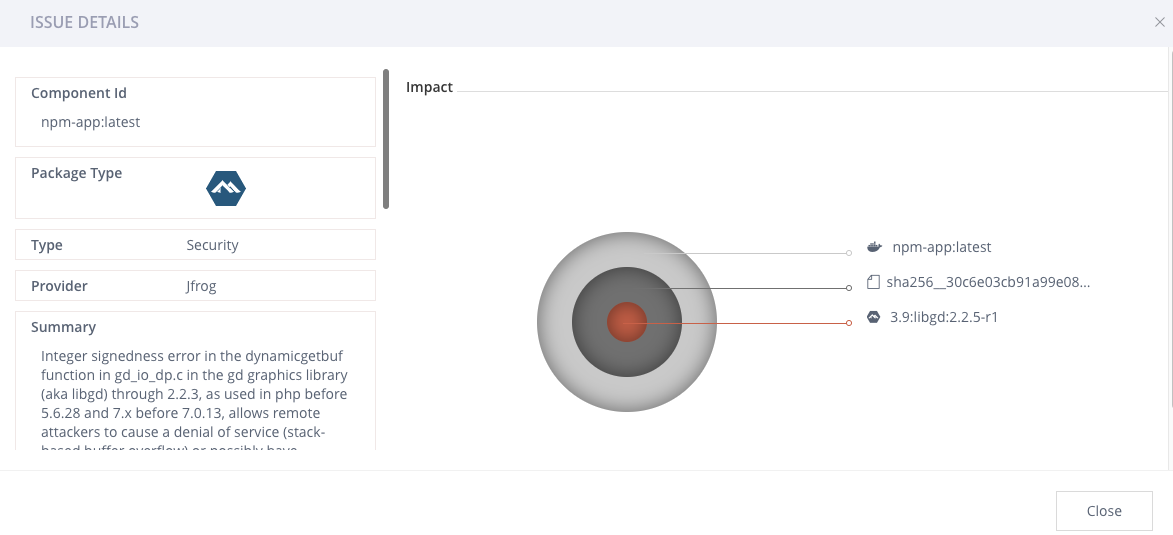
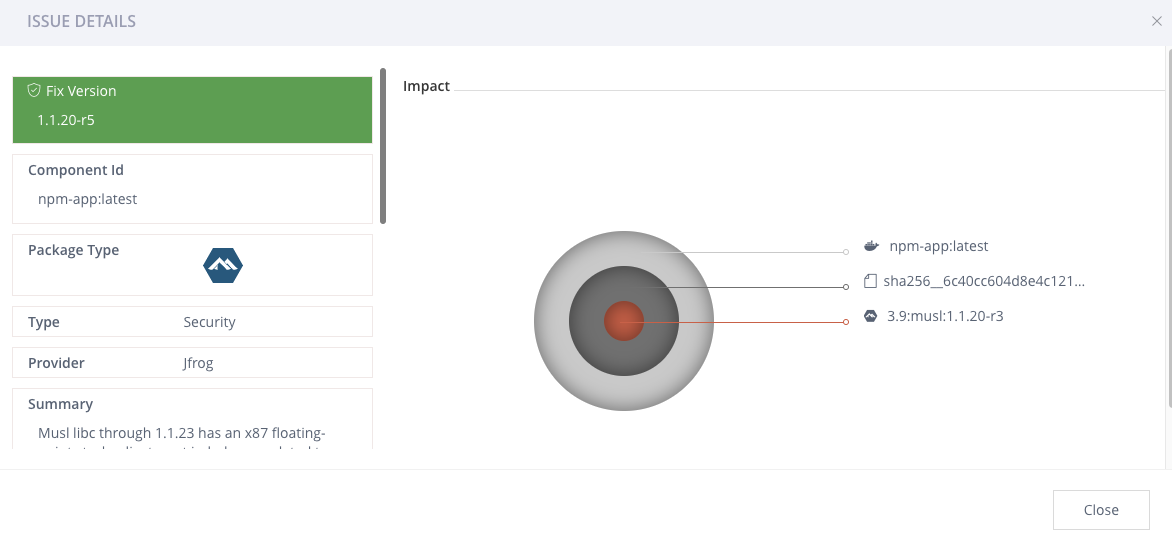
Click on any violation to see the details and impact in the Issue Details tab.
-
Scroll down to the References section to access links to documentation that can help you remediate the issue.
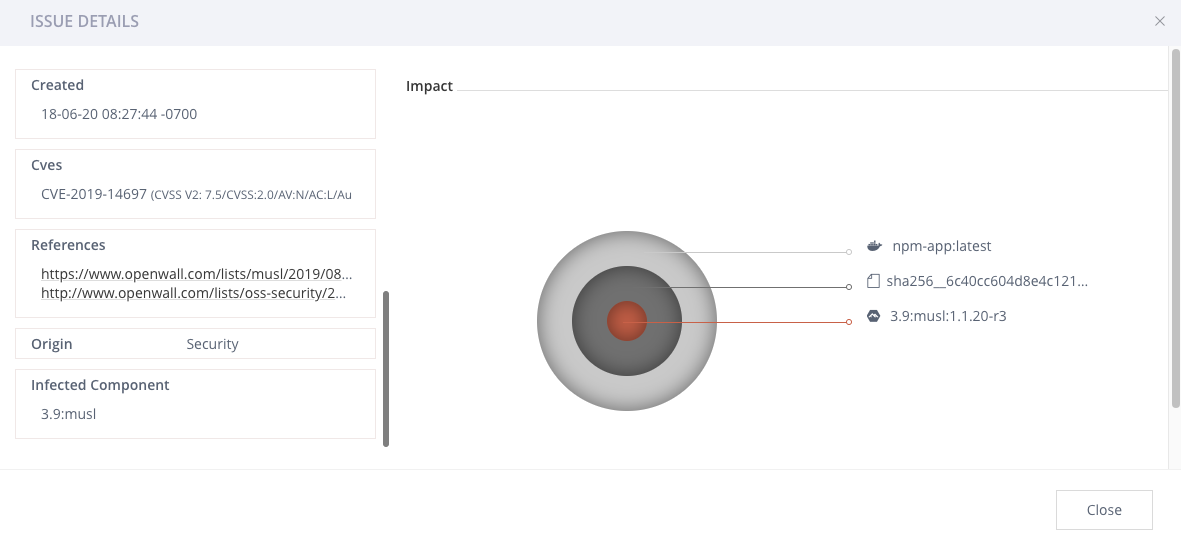
In many cases, you just need to update the component and Xray will indicate this.
Xray supports all major package types, understands how to unpack them, and uses recursive scanning to see into all of the underlying layers and dependencies of components, even those packaged in Docker images, and zip files. The comprehensive vulnerability intelligence databases are constantly updated giving the most up-to-date understanding of the security and compliance of your binaries and features like threat contextual analysis, git repo scanning, jira integration, SBOM support for the SPDX and CycloneDX standard formats and many more.
- Close the Issue Details tab.
- View the Docker configuration for the image in the Docker Layers tab.
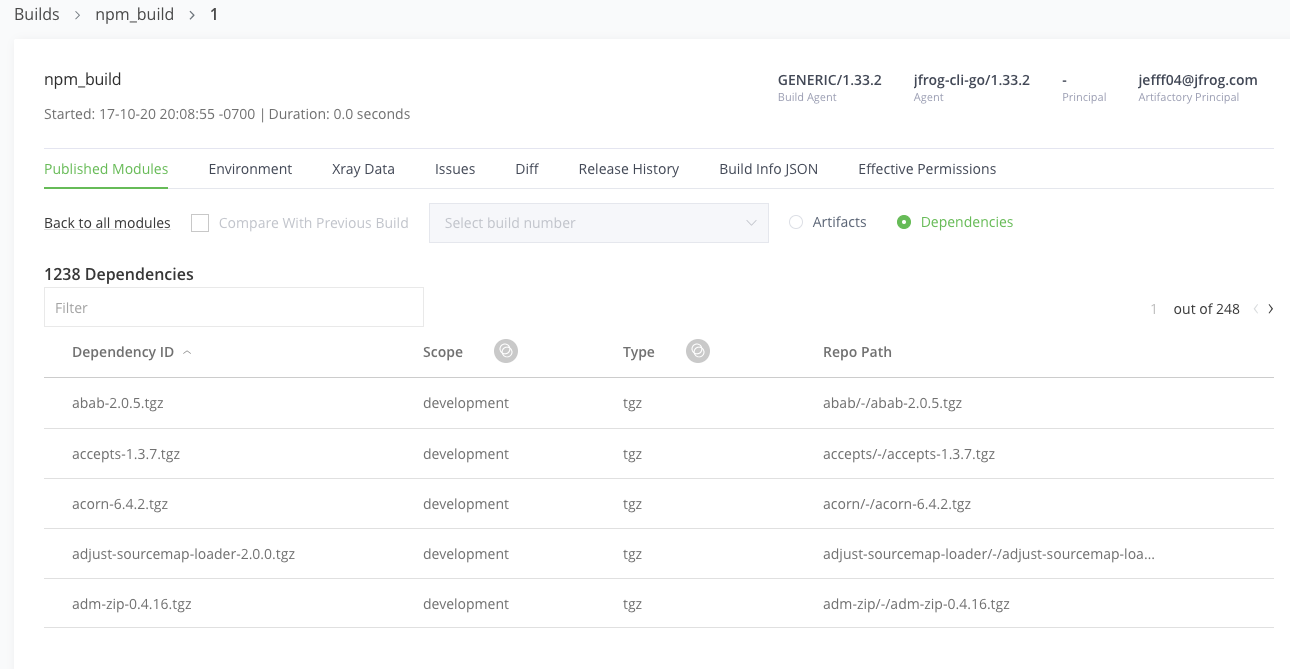
- On the Builds tab, click on npm_build in the list.
- Then click on your most recent build.
- In the Published Modules tab, view the set of artifacts and dependencies for your build.
Our JFrog CLI CI/CD “pipeline” provided an overview of a typical build, docker build and push, security scan and promotion process using Artifactory and Xray.