DevSecOps
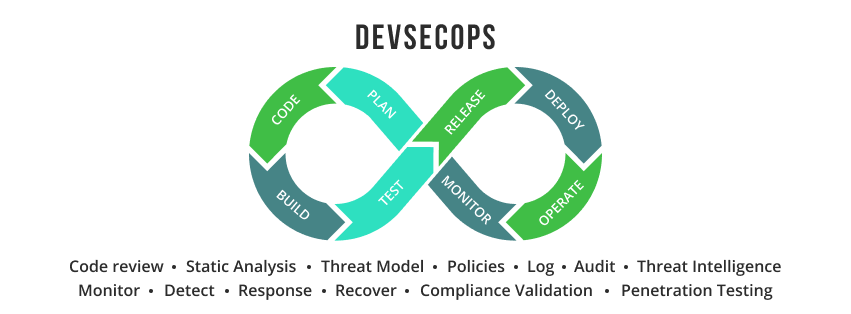
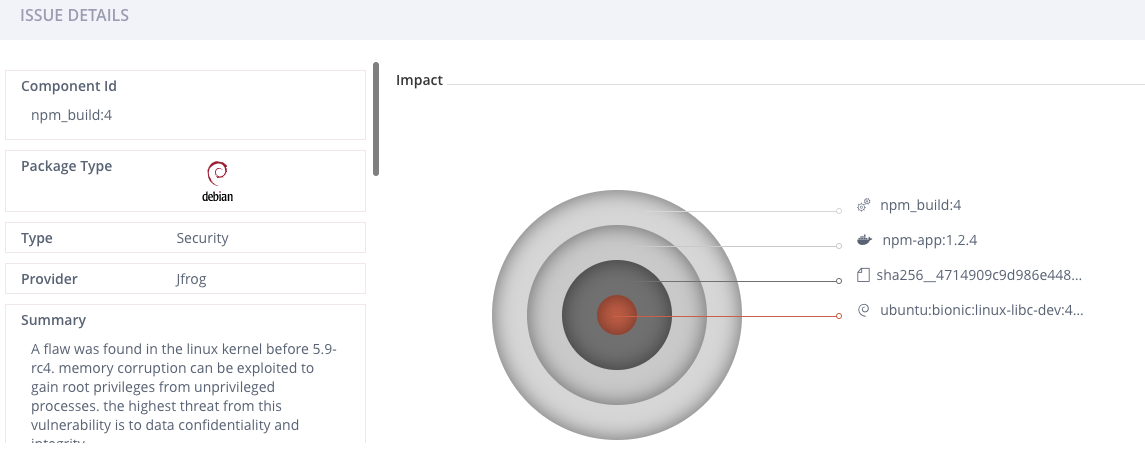
Any security issue identified by a security scanning may be reviewed by a small security team that may lack the technical knowledge. This challenge can be reduced by shifting left to the developer and operations teams, making them also responsible for security and compliance. This moves security earlier in the software delivery process. Source code, dependency and artifact security scanning are some examples of moving security into the development process. Implementing the identification of security issues earlier in the CI/CD pipeline, as well as automating security and compliance policies in the Software Development Lifecycle (SDLC), rather than using manual processes, is crucial. Moreover, organizations that leave the Sec out of DevOps, may face security and compliance issues that are closer to their release, resulting in additional costs for remediating such issues.
As you move your SDLC to the cloud, your DevSecOps strategy must also adapt to the cloud. As discussed previously, binary repository managers that scale globally across cloud data centers require DevSecOps tools that will likewise scale and adjust. An enterprise scale software delivery system with multiple development teams, end users and devices mean more entry points for potential security and compliance issues. Therefore, it is critical that your SLDC is well-integrated with your DevSecOps system.